Biometrics make use of our most unique physical features and behaviors to serve as digital identifiers that computers and software can interpret and utilize for identity-related applications. They can be used to identify someone in a biometric database or to verify the authenticity of a claimed identity.
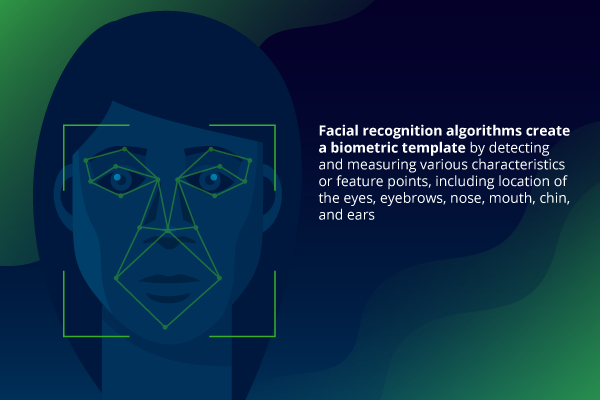
Facial recognition apps apply the science of biometrics to a user’s facial features. Facial recognition algorithms create a biometric template by detecting and measuring various characteristics, or feature points, of human faces, including location of the eyes, eyebrows, nose, mouth, chin, and ears. Two templates are compared to yield a match score, which indicates the likelihood that the two images belong to the same person. Liveness detection may also be applied to ensure that the source of the biometric sample is not a digital or paper reproduction.
Face Recognition Use cases
Law enforcement agencies such as the FBI use facial recognition technology to search criminal watch lists and help conclusively identify a person of interest. They can match a recently taken photo or video against a database of single images to help identify that person. Governments around the world use facial for biometric identification for a variety of applications including customs and border security, fraud prevention, and citizen ID.
More recently, mobile authentication has emerged as the most common main private-sector use case for facial biometrics, where our facial images can be used in place of a password. Users can log onto their devices using facial recognition as a convenient and secure alternative to PINs and passwords. Incorporating facial recognition into a mobile app, such as for banking or other secure applications, allows the app provider to have more control of the security features and user experience and also achieve more consistency across customer devices. Face recognition systems can also be used to enhance patient identification in healthcare settings.
Facial recognition’s advantages
Each biometric modality offers advantages and disadvantages. Facial recognition offers several advantages over other biometrics:
- Proliferation of digital facial image data: The billions of existing digital facial images from countless sources are extremely useful for algorithm training purposes, particularly for algorithms using machine learning techniques.
- Enhancement of manual facial recognition: Biometrics can be used in concert with human visual facial recognition processes, such as comparing a live person to their facial image on their driver’s licence or other ID card. Facial recognition technology can be used to automate or enhance this process and provides greater matching accuracy. For just about any process where a person’s face is used by a human to verify their identity, biometrics can be used to improve it.
- Ubiquity of cameras on mobile devices: Nearly all smartphones, tablets, and laptops have built-in front-facing cameras that enable high-quality “selfie” shots. This makes it convenient to collect a live facial recognition sample for comparison against a template.
- Conducive for use with other modalities for mobile authentication: Facial image capture using the front-facing camera on a phone can be performed passively and simultaneously during capture of other modalities such as voice and keystroke to improve matching performance and liveness detection.
Facial recognition’s challenges
The following challenges must be addressed for facial recognition apps to be useful:
- Wide variety of environmental capture conditions (e.g. lighting, shadows) make accurate matching more challenging. Pose variations, aging, glasses, facial expressions, and facial hair can also make matching more difficult. Differences between camera sensors and settings can also have an impact.
- High availability of facial images on social media and other mediums means fraudsters can more easily obtain images of potential fraud victims that can be used for spoofing. Unlike Face I.D. technology, which only detects the presence of a face in an image or video, face recognition apps work within algorithms that must also be able to tell a live face versus a non-live digital image of a face.
Fraudsters can exploit these challenges in a few ways.
First, they may try to bypass face biometrics used for authentication or access control by presenting a non-live image of an authorized user during the challenge.
Second, they may attempt to register for a new account by enrolling a face sample that cannot be accurately used in a deduplication search. For example, they could try to enroll a picture that distorts or obstructs facial features using makeup, hats, or sun glasses. They could also try to use a picture of a person who does not exist, or faces of celebrities pulled from the web. All of these would lead to false non-matches during identify verification searches.
Overcoming the challenges of face recognition
Several steps can be taken to optimize security, performance, and user experience.
Automate capture of high-quality images
Software for facial recognition that automates capture of facial images analyzes the streaming video frames in real time. Image capture is automatically triggered once focus, facial positioning, lighting, and other image-capture details are verified for compliance with quality standards.
The image is analyzed again and optimized post-capture. Automatic scaling, rotation, cropping, brightness, and contrast enhancements optimize the quality of an otherwise non-compliant image so the photo doesn’t have to be retaken.
Perform robust liveness detection
Fraudsters may attempt to spoof a facial recognition algorithm with non-live digital videos and images obtained online. Liveness detection algorithms distinguish between a printed, digital, video, and a live facial image.
Passive liveness detection looks for indicators of a non-live image such as inconsistent features between foreground and background. It uses various recognition techniques to search for artifacts in an image such as cutouts, masks, skin, texture, borders, and various other characteristics that help it determine a false representation of a user’s face. This process is invisible to the user, which makes it harder for fraudsters to bypass it.
Active liveness detection prompts the user to blink or shake his or her head to ascertain liveness.
The combination of active and passive methods will yield the highest performance matching. Facial recognition analysis applications might also leverage a second modality such as voice to help assure liveness.
Use high-performance algorithms
In the past few years, artificial intelligence and machine learning algorithms have become the predominant methods for automatically extracting the above information and then comparing it against other images. These algorithms enhance the biometric security of face recognition technology without having any impact on the user experience.
Aware’s facial recognition software products
Aware products for facial recognition:
- Knomi: Mobile authentication with facial matching and liveness detection.
- PreFace: Face image autocapture and processing on mobile device or desktop.
- Nexa|Face: Face recognition matching algorithm SDK.
- FaceWorkbench: Forensic examiner workstation application.
- AwareABIS: Automated biometric identification system.
Learn more about Aware’s portfolio of face recognition solutions and services.